Cisco lab - Test tính năng IPS trên Router Cisco
Để thực hiện bài test ta cần Router có kèm license Security, download Signature IPS mới nhất trên trang chủ Cisco (IOS-S1024-CLI.pkg) ở bài test này mình sẽ thực hiện test tính năng chống tấn công DoS dùng IPS trên Router. Dùng tool XOIC để thực hiện việc tấn công DoS đến Router.
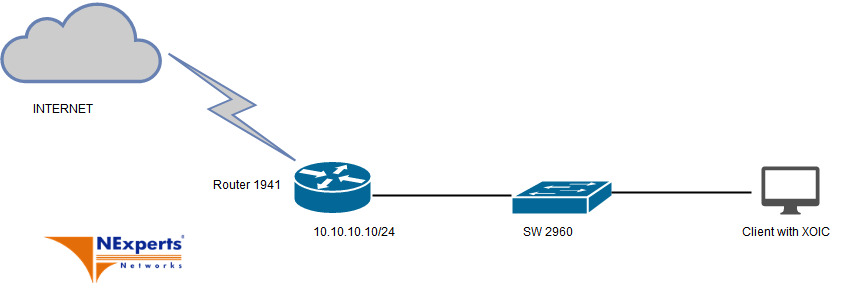
Các bước cấu hình trên Router:
1, Copy crypto key cho IOS-IPS:
crypto key pubkey-chain rsa
named-key realm-cisco.pub signature
key-string
30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101
00C19E93 A8AF124A D6CC7A24 5097A975 206BE3A2 06FBA13F 6F12CB5B 4E441F16
17E630D5 C02AC252 912BE27F 37FDD9C8 11FC7AF7 DCDD81D9 43CDABC3 6007D128
B199ABCB D34ED0F9 085FADC1 359C189E F30AF10A C0EFB624 7E0764BF 3E53053E
5B2146A9 D7A5EDE3 0298AF03 DED7A5B8 9479039D 20F30663 9AC64B93 C0112A35
FE3F0C87 89BCB7BB 994AE74C FA9E481D F65875D6 85EAF974 6D9CC8E3 F0B08B85
50437722 FFBE85B9 5E4189FF CC189CB9 69C46F9C A84DFBA5 7A0AF99E AD768C36
006CF498 079F88F8 A3B3FB1F 9FB7B3CB 5539E1D1 9693CCBB 551F78D2 892356AE
2F56D826 8918EF3C 80CA4F4D 87BFCA3B BFF668E9 689782A5 CF31CB6E B4B094D3
F3020301 0001
quit
exit
2, Tạo 1 thư mục trên flash để lưu trữ Signature IPS:
mkdir IPSIOS
ip ips name IPS_VNE
ip ips config location flash:IPSIOS
3, Enable các Catagory cần thiết:
ip ips signature-category
category all
alert-severity high
retired true
category ddos all-ddos
event-action deny-attacker-inline produce-alert
category dos tcp_floods
event-action deny-attacker-inline
category dos udp_floods
event-action deny-attacker-inline produce-alert
category dos icmp_floods
enabled true
event-action deny-connection-inline deny-attacker-inline
4, Áp dụng IOS IPS vào internface:
interface GigabitEthernet0/0
ip address 10.10.10.10 255.255.255.0
ip ips IPS_VNE in
ip ips IPS_VNE out
duplex auto
speed auto
5, Sau khi download Signature mới nhất ta tiến hành copy và compile:
copy tftp://10.10.10.1/IOS-S1024-CLI.pkg idconf
note: việc này có thể khiến CPU của router đạt đến ngưỡng 100%
Trên Client thực hiện việc tấn công DoS vào Router:
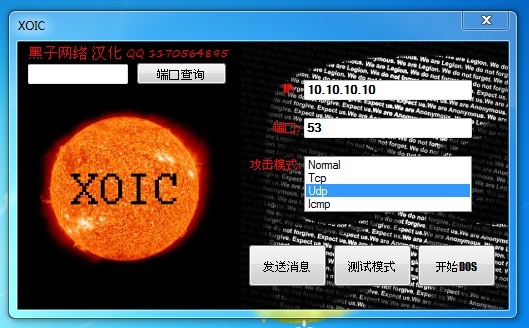
Kết quả:
Kiểm tra logg trên router phương thức tấn công đã bị từ chối:
Router#show logging
Syslog logging: enabled (19054 messages dropped, 2 messages rate-limited, 154424 flushes, 0 overruns, xml disabled, filtering disabled)
No Active Message Discriminator.
No Inactive Message Discriminator.
Console logging: level debugging, 405561 messages logged, xml disabled,
filtering disabled
Monitor logging: level debugging, 0 messages logged, xml disabled,
filtering disabled
Buffer logging: level debugging, 223712 messages logged, xml disabled,
filtering disabled
Exception Logging: size (4096 bytes)
Count and timestamp logging messages: disabled
Persistent logging: disabled
No active filter modules.
Trap logging: level informational, 139 message lines logged
Logging Source-Interface: VRF Name:
Log Buffer (8192 bytes):
ion: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.235: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.235: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.235: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.235: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.235: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.235: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.235: IPS CAT -- Found keyname dos
*Nov 12 09:41:03.235: IPS CAT -- Found keyname tcp_floods
*Nov 12 09:41:03.235: IPS CAT -- Element match found
*Nov 12 09:41:03.235: SME:atomic-ip sig:3051 index:1
*Nov 12 09:41:03.235: event action: deny-attacker-inline
*Nov 12 09:41:03.235: SME:atomic-ip sig:3051 index:1
*Nov 12 09:41:03.235: event action: deny-attacker-inline
*Nov 12 09:41:03.239: SME:string-tcp sig:3178 index:8
*Nov 12 09:41:03.239: event action: deny-attacker-inline
*Nov 12 09:41:03.239: SME:atomic-ip sig:3300 index:1
*Nov 12 09:41:03.239: event action: deny-attacker-inline
*Nov 12 09:41:03.239: SME:string-tcp sig:3344 index:8
*Nov 12 09:41:03.239: event action: deny-attacker-inline
*Nov 12 09:41:03.239: SME:atomic-ip sig:3345 index:1
*Nov 12 09:41:03.239: event action: deny-attacker-inline
*Nov 12 09:41:03.243: SME:string-tcp sig:3653 index:8
*Nov 12 09:41:03.243: event action: deny-attacker-inline
*Nov 12 09:41:03.247: SME:service-http sig:3665 index:3
*Nov 12 09:41:03.247: event action: deny-attacker-inline
*Nov 12 09:41:03.247: SME:atomic-ip sig:4068 index:1
*Nov 12 09:41:03.247: event action: deny-attacker-inline
*Nov 12 09:41:03.247: SME:service-http sig:4131 index:3
*Nov 12 09:41:03.247: event action: deny-attacker-inline
*Nov 12 09:41:03.247: SME:atomic-ip sig:5222 index:1
*Nov 12 09:41:03.247: event action: deny-attacker-inline
*Nov 12 09:41:03.251: SME:string-tcp sig:5784 index:8
*Nov 12 09:41:03.251: event action: deny-attacker-inline
*Nov 12 09:41:03.255: SME:string-tcp sig:5785 index:8
*Nov 12 09:41:03.255: event action: deny-attacker-inline
*Nov 12 09:41:03.255: SME:string-tcp sig:5786 index:8
*Nov 12 09:41:03.255: event action: deny-attacker-inline
*Nov 12 09:41:03.259: SME:string-tcp sig:5787 index:8
*Nov 12 09:41:03.259: event action: deny-attacker-inline
*Nov 12 09:41:03.259: SME:string-tcp sig:5788 index:8
*Nov 12 09:41:03.259: event action: deny-attacker-inline
*Nov 12 09:41:03.259: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.263: event action: deny-attacker-inline
*Nov 12 09:41:03.267: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.267: event action: deny-attacker-inline
*Nov 12 09:41:03.267: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.267: event action: deny-attacker-inline
*Nov 12 09:41:03.267: SME:atomic-ip sig:6009 index:1
*Nov 12 09:41:03.267: event action: deny-attacker-inline
*Nov 12 09:41:03.271: SME:service-http sig:38846 index:3
*Nov 12 09:41:03.271: event action: deny-attacker-inline
*Nov 12 09:41:03.271: IPS CAT -- Found keyname dos
*Nov 12 09:41:03.271: IPS CAT -- Found keyname udp_floods
*Nov 12 09:41:03.271: IPS CAT -- Element match found
*Nov 12 09:41:03.275: SME:atomic-ip sig:4061 index:1
*Nov 12 09:41:03.275: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.279: SME:string-udp sig:4513 index:11
*Nov 12 09:41:03.279: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.283: SME:string-udp sig:4608 index:11
*Nov 12 09:41:03.283: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.287: SME:string-udp sig:4608 index:11
*Nov 12 09:41:03.287: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.287: SME:string-udp sig:4608 index:11
*Nov 12 09:41:03.291: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.291: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.291: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.291: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.291: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.291: SME:atomic-ip sig:4608 index:1
*Nov 12 09:41:03.291: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.291: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.291: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.295: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.295: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.295: SME:atomic-ip sig:5835 index:1
*Nov 12 09:41:03.295: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.295: SME:atomic-ip sig:5912 index:1
*Nov 12 09:41:03.295: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.299: SME:atomic-ip sig:15016 index:1
*Nov 12 09:41:03.299: event action: deny-attacker-inline|produce-alert
*Nov 12 09:41:03.299: IPS CAT -- Found keyname dos
*Nov 12 09:41:03.299: IPS CAT -- Found keyname icmp_floods
*Nov 12 09:41:03.299: IPS CAT -- Element match found
*Nov 12 09:41:03.307: SME:atomic-ip sig:2157 index:1
*Nov 12 09:41:03.307: enable: true
*Nov 12 09:41:03.307: event action: deny-connection-inline|deny-attacker-inline
*Nov 12 09:41:03.307: SME:atomic-ip sig:2157 index:1
*Nov 12 09:41:03.307: enable: true
*Nov 12 09:41:03.307: event action: deny-connection-inline|deny-attacker-inline
*Nov 12 09:41:03.307: SME:atomic-ip sig:2157 index:1
*Nov 12 09:41:03.307: enable: true
*Nov 12 09:41:03.307: event action: deny-connection-inline|deny-attacker-inline
*Nov 12 09:41:03.307: SME:atomic-ip sig:2769 index:1
*Nov 12 09:41:03.307: enable: true
*Nov 12 09:41:03.307: event action: deny-connection-inline|deny-attacker-inline
*Nov 12 09:41:09.999: %IPS-5-PACKET_UNSCANNED: atomic-ip - fail open - packets passed unscanned
*Nov 12 09:41:09.999: %IPS-6-ENGINE_READY: atomic-ip - build time 6276 ms - packets for this engine will be scanned
*Nov 12 09:41:10.247: %IPS-6-ENGINE_BUILDING: normalizer - 10 signatures - 2 of 13 engines
*Nov 12 09:41:10.247: %IPS-6-ENGINE_READY: normalizer - build time 0 ms - packets for this engine will be scanned
*Nov 12 09:41:10.867: %IPS-6-ENGINE_BUILDING: service-http - 2064 signatures - 3 of 13 engines
*Nov 12 09:41:18.411: %IPS-6-ENGINE_READY: service-http - build time 7544 ms - packets for this engine will be scanned
*Nov 12 09:41:18.863: %IPS-6-ENGINE_BUILDING: service-smb-advanced - 77 signatures - 4 of 13 engines
*Nov 12 09:41:18.983: %IPS-6-ENGINE_READY: service-smb-advanced - build time 120 ms - packets for this engine will be scanned
*Nov 12 09:41:19.011: %IPS-6-ENGINE_BUILDING: service-msrpc - 37 signatures - 5 of 13 engines
*Nov 12 09:41:19.371: %IPS-6-ENGINE_READY: service-msrpc - build time 360 ms - packets for this engine will be scanned
*Nov 12 09:41:19.391: %IPS-6-ENGINE_BUILDING: state - 39 signatures - 6 of 13 engines
*Nov 12 09:41:19.399: %IPS-6-ENGINE_READY: state - build time 8 ms - packets for this engine will be scanned
*Nov 12 09:41:19.407: %IPS-6-ENGINE_BUILDING: service-ftp - 3 signatures - 7 of 13 engines
*Nov 12 09:41:19.407: %IPS-6-ENGINE_READY: service-ftp - build time 0 ms - packets for this engine will be scanned
*Nov 12 09:41:20.643: %IPS-6-ENGINE_BUILDING: string-tcp - 4481 signatures - 8 of 13 engines
*Nov 12 09:41:22.179: %IPS-6-ENGINE_READY: string-tcp - build time 1536 ms - packets for this engine will be scanned
*Nov 12 09:41:23.039: %IPS-6-ENGINE_BUILDING: service-rpc - 79 signatures - 9 of 13 engines
*Nov 12 09:41:23.075: %IPS-6-ENGINE_READY: service-rpc - build time 36 ms - packets for this engine will be scanned
*Nov 12 09:41:23.111: %IPS-6-ENGINE_BUILDING: service-dns - 44 signatures - 10 of 13 engines
*Nov 12 09:41:23.131: %IPS-6-ENGINE_READY: service-dns - build time 20 ms - packets for this engine will be scanned
*Nov 12 09:41:23.159: %IPS-6-ENGINE_BUILDING: string-udp - 74 signatures - 11 of 13 engines
*Nov 12 09:41:23.215: %IPS-6-ENGINE_READY: string-udp - build time 56 ms - packets for this engine will be scanned
*Nov 12 09:41:23.999: %IPS-6-ENGINE_BUILDING: multi-string - 1109 signatures - 12 of 13 engines
*Nov 12 09:41:24.963: %IPS-6-ENGINE_READY: multi-string - build time 964 ms - packets for this engine will be scanned
*Nov 12 09:41:25.459: %IPS-6-ALL_ENGINE_BUILDS_COMPLETE: elapsed time 22140 ms
*Nov 12 09:41:25.459: %SYS-5-CONFIG_I: Configured from console by console
Cấu hình hoàn chỉnh:
Router#show running-config
Building configuration...
Current configuration : 4415 bytes
!
! Last configuration change at 09:41:25 UTC Mon Nov 12 2018
version 15.3
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot system flash:c1900-universalk9-mz.SPA.153-3.M4.bin
boot-end-marker
!
!
!
no aaa new-model
!
!
!
!
!
!
!
ip ips config location flash:IPSIOS retries 1
ip ips notify SDEE
ip ips name IPS_VNE
!
ip ips signature-category
category all
alert-severity high
retired true
category viruses/worms/trojans all-viruses/worms/trojans
event-action deny-attacker-inline
category p2p bittorrent
event-action deny-attacker-inline
category ios_ips basic
retired false
category ios_ips advanced
retired false
category ddos all-ddos
event-action deny-attacker-inline produce-alert
category dos tcp_floods
event-action deny-attacker-inline
category dos udp_floods
event-action deny-attacker-inline produce-alert
category dos icmp_floods
enabled true
event-action deny-connection-inline deny-attacker-inline
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
crypto pki trustpoint TP-self-signed-4067250037
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4067250037
revocation-check none
rsakeypair TP-self-signed-4067250037
!
!
crypto pki certificate chain TP-self-signed-4067250037
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34303637 32353030 3337301E 170D3138 31313132 30333235
30345A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 30363732
35303033 3730819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
81009611 48D3E6A5 2FD17929 11179DBD 53F84D07 0362065A 295AB530 14301D84
287A1722 6B3AED66 E4FE1961 3442648A 68CEB3D5 6E849842 800EE926 DD60FA8D
D4BA72E1 46BC8166 0AD15471 B5D803D7 926F24BE DE94AFF3 E50C4922 4087B1CC
4A22C195 7594F2BB C7777FAB 3AD0E396 F3E95BF5 4F66D679 288E4BC9 6F144223
5DE90203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 14CFFDAE 6BF145AC 80540DBB 92695F65 C2E75872 FD301D06
03551D0E 04160414 CFFDAE6B F145AC80 540DBB92 695F65C2 E75872FD 300D0609
2A864886 F70D0101 05050003 8181008A 9E2F3067 0823F930 659567F0 4CE4F14F
56CF6F4C 43FE945A 83572D67 E1C38F84 BAC5B9AB 93741DB7 358892ED 96F9B85D
F11724E1 A74C6F67 5B31312A 8AA33676 9A7F0C9A 7831B777 137FD350 01A7C010
524A9232 EF47FE23 44E1939A 6E80AE77 F38F89BF 24934BB5 FFC60CC8 FC1E64CE
FB711F9F FB310A57 A486E6BF 337250
quit
license udi pid CISCO1941/K9 sn FHKXXXXXXX
license boot module c1900 technology-package securityk9
!
!
username cisco privilege 15 password 0 cisco
!
redundancy
!
crypto key pubkey-chain rsa
named-key realm-cisco.pub signature
key-string
30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101
00C19E93 A8AF124A D6CC7A24 5097A975 206BE3A2 06FBA13F 6F12CB5B 4E441F16
17E630D5 C02AC252 912BE27F 37FDD9C8 11FC7AF7 DCDD81D9 43CDABC3 6007D128
B199ABCB D34ED0F9 085FADC1 359C189E F30AF10A C0EFB624 7E0764BF 3E53053E
5B2146A9 D7A5EDE3 0298AF03 DED7A5B8 9479039D 20F30663 9AC64B93 C0112A35
FE3F0C87 89BCB7BB 994AE74C FA9E481D F65875D6 85EAF974 6D9CC8E3 F0B08B85
50437722 FFBE85B9 5E4189FF CC189CB9 69C46F9C A84DFBA5 7A0AF99E AD768C36
006CF498 079F88F8 A3B3FB1F 9FB7B3CB 5539E1D1 9693CCBB 551F78D2 892356AE
2F56D826 8918EF3C 80CA4F4D 87BFCA3B BFF668E9 689782A5 CF31CB6E B4B094D3
F3020301 0001
quit
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
ip address 10.10.10.10 255.255.255.0
ip ips IPS_VNE in
ip ips IPS_VNE out
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0/0
no ip address
shutdown
clock rate 2000000
!
ip forward-protocol nd
!
ip http server
ip http authentication local
ip http secure-server
!
!
!
!
!
control-plane
!
!
!
line con 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
login
transport input all
!
scheduler allocate 20000 1000
!
end
==========================================================================
Router#show ip ips configuration
IPS Signature File Configuration Status
Configured Config Locations: flash:IPSIOS
Last signature default load time: 06:41:08 UTC Nov 12 2018
Last signature delta load time: 09:41:25 UTC Nov 12 2018
Last event action (SEAP) load time: -none-
General SEAP Config:
Global Deny Timeout: 3600 seconds
Global Overrides Status: Enabled
Global Filters Status: Enabled
IPS Auto Update is not currently configured
IPS Syslog and SDEE Notification Status
Event notification through syslog is enabled
Event notification through SDEE is enabled
IPS Signature Status
Total Active Signatures: 586
Total Inactive Signatures: 8029
IPS Packet Scanning and Interface Status
IPS Rule Configuration
IPS name IPS_VNE
IPS fail closed is disabled
IPS deny-action ips-interface is false
Obsolete tuning is disabled
Regex compile threshold (MB) 31
Interface Configuration
Interface GigabitEthernet0/0
Inbound IPS rule is IPS_VNE
Outgoing IPS rule is IPS_VNE
IPS Category CLI Configuration:
Category all:
Alert Severity: High
Retire: True
Category viruses/worms/trojans all-viruses/worms/trojans: Deny-attacker
Category p2p bittorrent: Deny-attacker
Category ios_ips basic:
Retire: False
Category ios_ips advanced:
Retire: False
Category ddos all-ddos: Deny-attacker Alert
Category dos tcp_floods: Deny-attacker
Category dos udp_floods: Deny-attacker Alert
Category dos icmp_floods:
Enable: True Deny-connection Deny-attacker
IPS License Status: Not Required
Current Date: Nov 12 2018
Expiration Date: Not Available
Extension Date: Not Available
Signatures Loaded: Oct 30 2018 S1024.0
Signature Package: Oct 30 2018 S1024.0
